“When is this going to end?” you’ve probably asked yourself, after hearing about the Home Depot data breach of up to 60 million consumer credit cards. The breach is the latest–and possibly largest–of a series of massive exposures of sensitive consumer information over the past few months.
The simple answer to your question: Not anytime soon.
In the five months since April 16, when I wrote one of my final blogs as Consumer Reports’s Technology Editor, entitled Another breach like Target’s is inevitable, we’ve seen more than just “another” such breach. We’ve seen several:
• In April, AOL notified millions of users that their user e-mail addresses and passwords may have been compromised.
• In May, eBay asked millions of its users to change their passwords after a reported 145 million records were exposed.
• In early August, Hold security (which had reported a massive data breach at Adobe in late 2013) reported that Russian hackers had amassed one billion user names and passwords stolen from 420,000 web sites.
• In late August, UPS (United Parcel Service) announced that credit card data for customers in 24 states may have been exposed.
In all, according to the Privacy Rights Clearinghouse, more than 200 breaches have been reported so far in 2014, resulting in the exposure of at least 7.5 million records.
Why the breaches keep coming

Cybercrime is a massive multinational industry that regularly makes many attempts to breach major institutions. Why so many of those efforts have been succeeding lately, on such a large scale, is due partly to how smart an organization needs to be to defend against them.
As security expert and author Jim Manico, head of Manicode Security, put it to me a couple of days ago in an e-mail, no silver bullet can prevent these massive breaches. It takes hard work. “Under these circumstances, no product, service or consultant will solve these security problems,” he wrote. “Security is not a product, a process or a person, but the harmony of good engineering that spans all of these things. Target at least did not have this harmony in play and paid the price dearly.”
But leaving it at “defense is hard” would be to excuse the organizations we entrust with our data for failing to do their job. The fact is, many retailers and website operators–large and small–have yet to earn our trust. In May, for example, I reported on widespread lax security and complacency among small retailers.
Large organizations like Target and Home Depot, with highly-trained, dedicated IT departments, have less excuse. As security expert Jeff Williams, now the Chief Technology Officer of Contrast Security, told me in April, when we discussed the inevitability of another massive breach like Target’s, “The problem is systemic…the security practices Target used are widespread.” Those included failing to respond to automated warnings about intruders and not isolating the most sensitive network assets.
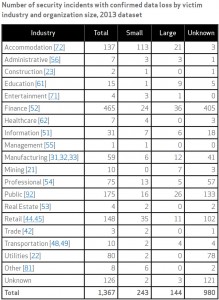
Statistics from 2013 support Williams’ assertion. This table from Verizon’s 2014 Data Breach Investigation Report shows how the most serious data breaches in what Verizon called the “year of the retail breach” were widely distributed among organizations of all sizes and industries:
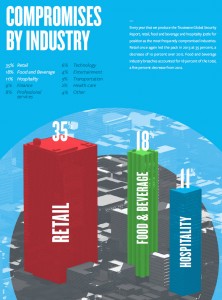
The chart below from the 2014 TrustWave Global Security Report shows how retailers, food and beverage firms, and hotel/motel outlets tended to suffer the most security breaches in 2013.
Lessons learned
I asked Williams to reflect on the accuracy of his prediction last May. “Well, you always feel terrible when a bad prediction comes true,” he told me. “But it’s easy to see when you look at the trends. Enterprises are busy automating their business at a record pace, digitizing more and more critical assets and functions, interconnecting systems like never before, and creating increasingly complex code. It’s the perfect storm for security issues.”
What have you learned from the latest breach at Home Depot? I asked. “I learned that other companies are not learning from the mistakes of their peers and competitors,” Williams responded. “When Target was breached, and their CEO and CIO fired, I would have expected other large retailers to take a really hard look at their POS [point of sale] systems. But here we are with another potentially gargantuan breach. I wonder if other companies will get the message this time. Of course, it’s easy to focus on the one security problem where someone just got hit. But the forward looking companies will see this trend and up their game across their entire enterprise.”
How can you protect yourself?
You can’t prevent a breach by a retailer or web site you patronize. But here are three measures you can take to minimize your own risk should such a breach occur:
• Use a credit card instead of a debit card. It has stronger legal protections.
• For the few sites with the greatest potential risk, such as financial institutions or those that store your credit card, use a strong password that you do not use at any other site. Then, if your password at a less important site is exposed, it can’t be used to compromise the important accounts.
• Regularly monitor your credit card and financial statements for unauthorized transactions. The sooner you spot any, the less damage you’ll suffer.
Industry’s dirty secret is out. Now what?
At security conferences over the past few years, I’ve heard security experts regularly lament such widespread lack of security preparedness–even on the part of some very large and respected brands. But until the Target breach, the public remained blissfully unaware of just how vulnerable to hackers some big household names really were. Even now, after all that has happened, few outside the security community and law enforcement appreciate the true size and scope of institutional vulnerability.
In the wake of this year’s massive breaches, is there any hope for a solution? “The situation is not hopeless,” Jeff Williams told me. “I have huge optimism about the use of automated security sensors in our development and operational environments. These sensors gather security critical data continuously and in real time – making security considerably more effective, complete, and efficient.”
To find out what the rest of the security industry thinks, next week I’ll be at AppSecUSA2014, one of the largest national security conferences. From there I’ll report back here at StateoftheNet.Net about the latest thinking in the ongoing effort to establish online security.
–Jeff Fox